Security in blockchain systems is often described in terms of cryptography and consensus, but for users, it is experienced more practically: transactions should execute exactly as intended, remain private where required, and resist manipulation or censorship. The Walrus protocol approaches transaction security as a layered discipline rather than a single mechanism. Built on the Sui blockchain and designed for privacy-preserving decentralized storage and interaction, Walrus combines cryptographic safeguards, verifiable execution, and economic incentives to protect users at every step of a transaction’s lifecycle.
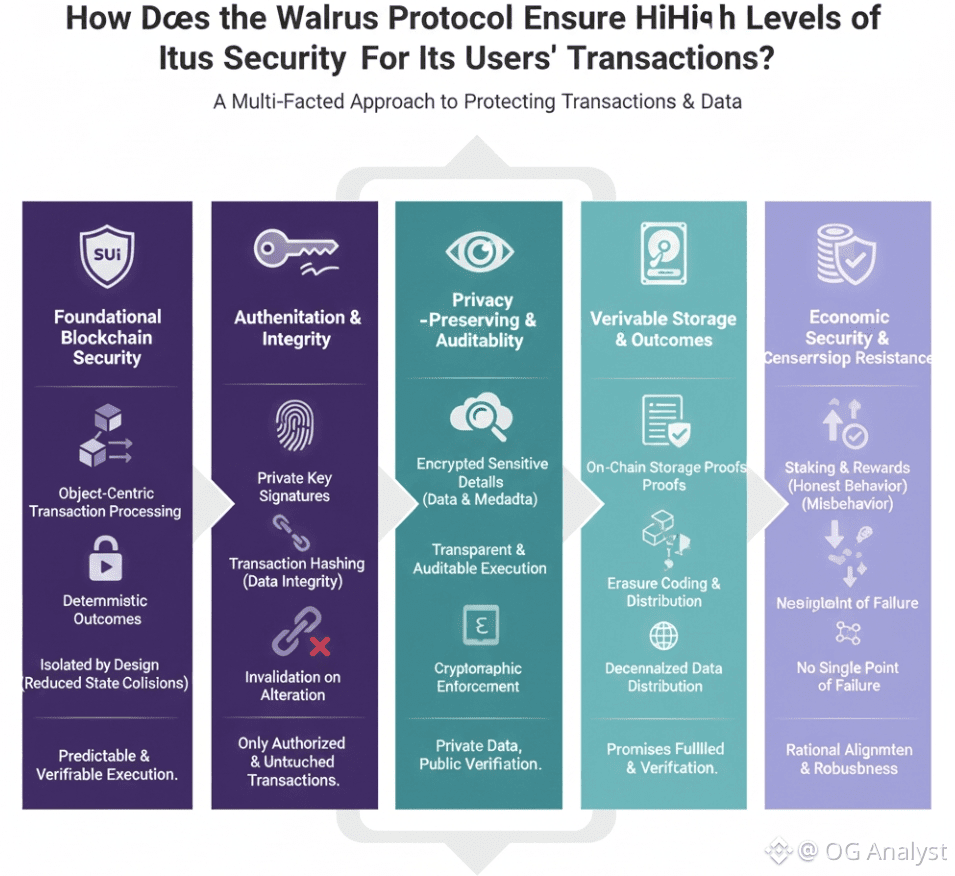
Security Begins with the Underlying Blockchain
Walrus inherits its foundational security properties from Sui, a blockchain designed around object-centric execution and parallel transaction processing. This architecture reduces shared global state, which in turn lowers the risk of unintended transaction interference.
For users, this means transactions are:
Deterministic – The outcome of a transaction is predictable and not dependent on unrelated network activity.
Isolated by design – Transactions interact only with the specific objects they reference, reducing attack surfaces such as state collisions or race conditions.
Final and verifiable – Once confirmed, transaction results are cryptographically secured and cannot be altered.
By building on this model, Walrus avoids many of the systemic risks that arise in more monolithic execution environments.
Cryptographic Integrity and Authentication
Every transaction within Walrus is secured through standard but rigorously applied cryptographic techniques. Users sign transactions with private keys, ensuring that only authorized parties can initiate actions such as storing data, retrieving files, or interacting with protocol services.
Beyond authentication, cryptographic hashing ensures that transaction payloads and references remain tamper-proof. Any alteration to a transaction—intentional or accidental—invalidates its signature, making manipulation immediately detectable.
This guarantees that what a user submits is exactly what the network executes.
Privacy Without Sacrificing Verifiability
Walrus is designed for environments where privacy matters, particularly around data interactions. While transaction execution remains transparent and auditable on-chain, sensitive details such as data contents and certain metadata are protected through encryption and hashing.
This separation is deliberate:
Transactions are verifiable – Observers can confirm that actions occurred correctly.
Sensitive details remain private – Data contents and contextual metadata are not exposed to the public.
Security does not rely on obscurity – Privacy is enforced cryptographically, not through hidden logic.
As a result, users gain confidence that their transactions are both secure and discreet.
Verifiable Storage and Transaction Outcomes
In Walrus, many transactions involve data storage or retrieval rather than simple value transfer. Security here depends on ensuring that transactional promises are actually fulfilled.
This is achieved through on-chain storage proofs. When a transaction results in data being stored, storage providers must later prove—cryptographically—that they continue to hold the correct data fragments. These proofs are recorded on-chain, creating an immutable audit trail.
For users, this means transaction outcomes are not just assumed; they are continuously verified over time.
Economic Security Through Incentives and Penalties
Walrus complements technical security with economic security. Storage providers stake value and earn rewards only if they behave correctly. Failing to serve data, submitting invalid proofs, or participating in malicious behavior can result in penalties or loss of rewards.
This incentive structure aligns rational behavior with honest behavior. Attacking the system or undermining transactions becomes economically irrational for participants, reinforcing security at the human and organizational level.
Resilience Against Censorship and Interference
Transaction security also includes resistance to suppression. Walrus distributes data and transaction effects across many independent nodes using erasure coding and decentralized verification. No single operator can block or reverse legitimate user transactions without coordinating a costly and visible attack across the network.
This resilience ensures that transactions are not only secure in execution but also reliably accessible, even under adverse conditions.
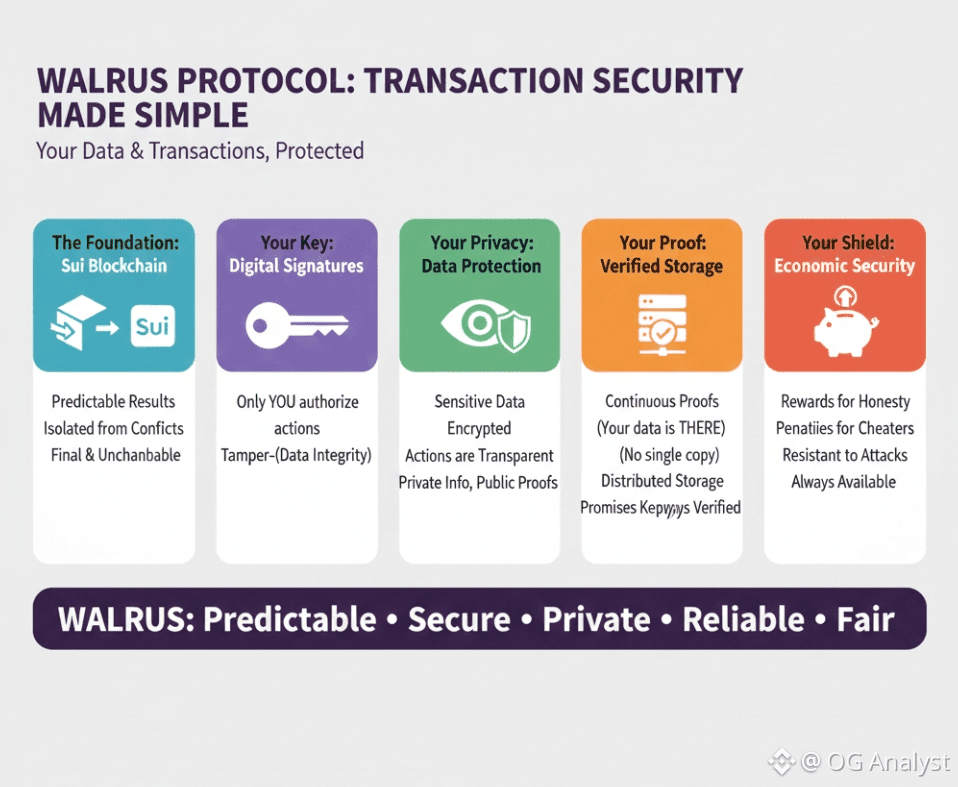
Conclusion
The Walrus protocol ensures high levels of transaction security by combining a secure underlying blockchain, strong cryptographic guarantees, privacy-preserving verification, continuous storage proofs, and incentive-aligned economics. Security is not treated as a single feature but as a system-wide property that spans execution, data integrity, privacy, and accountability.
For users, this results in transactions that are predictable, verifiable, resistant to manipulation, and protected against both technical and economic threats. In Walrus, transaction security is not an abstraction—it is a practical outcome of deliberate design choices made at every layer of the protocol.




