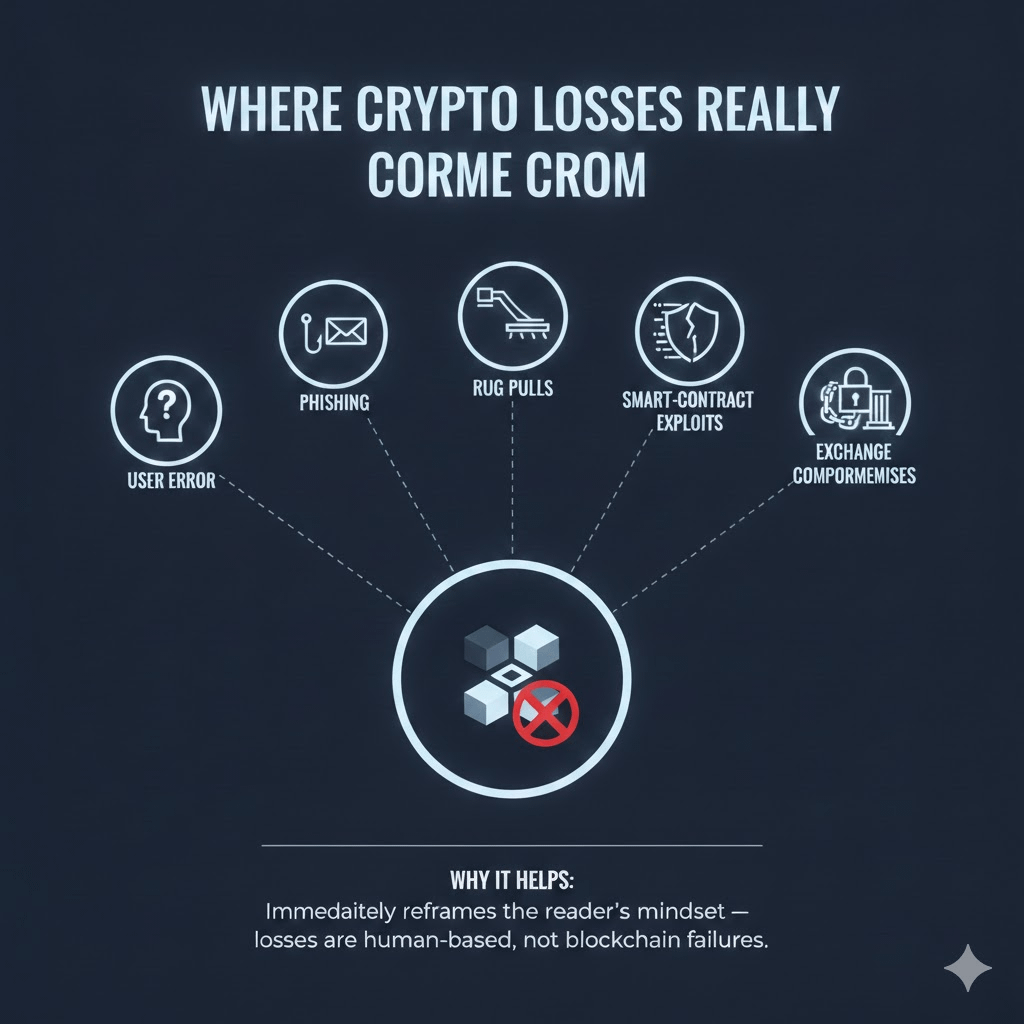
As cryptocurrency adoption grows, so does the sophistication of scams and security threats. While blockchain technology itself is secure, users remain the weakest link. Every year, billions of dollars are lost not because blockchains fail but because people fall victim to fraud, phishing, fake platforms, and poor security practices.
Understanding how crypto scams work and how to protect yourself is no longer optional. It’s a core skill for every trader, investor, and long-term holder.
This guide breaks down common crypto scams, real security risks, and practical steps anyone from beginners to advanced users can take to stay safe.
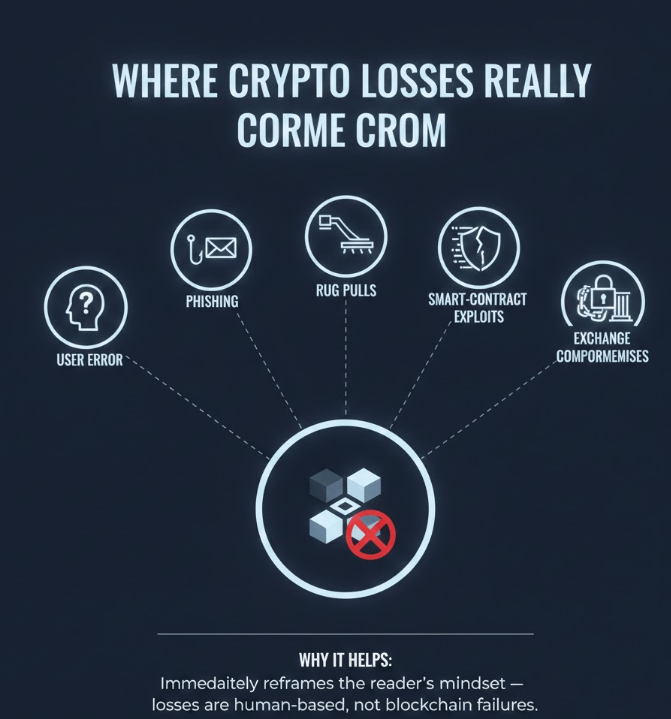
Why Crypto Security Matters
Unlike traditional banking, crypto transactions are:
Irreversible
Permissionless
Self-custodied
If funds are sent to a scammer or a wallet is compromised, recovery is often impossible. There’s no “customer support” to reverse mistakes. That’s why education is your strongest defense.
Common Types of Crypto Scams You Must Know
Phishing Scams
Phishing is the most widespread crypto scam.
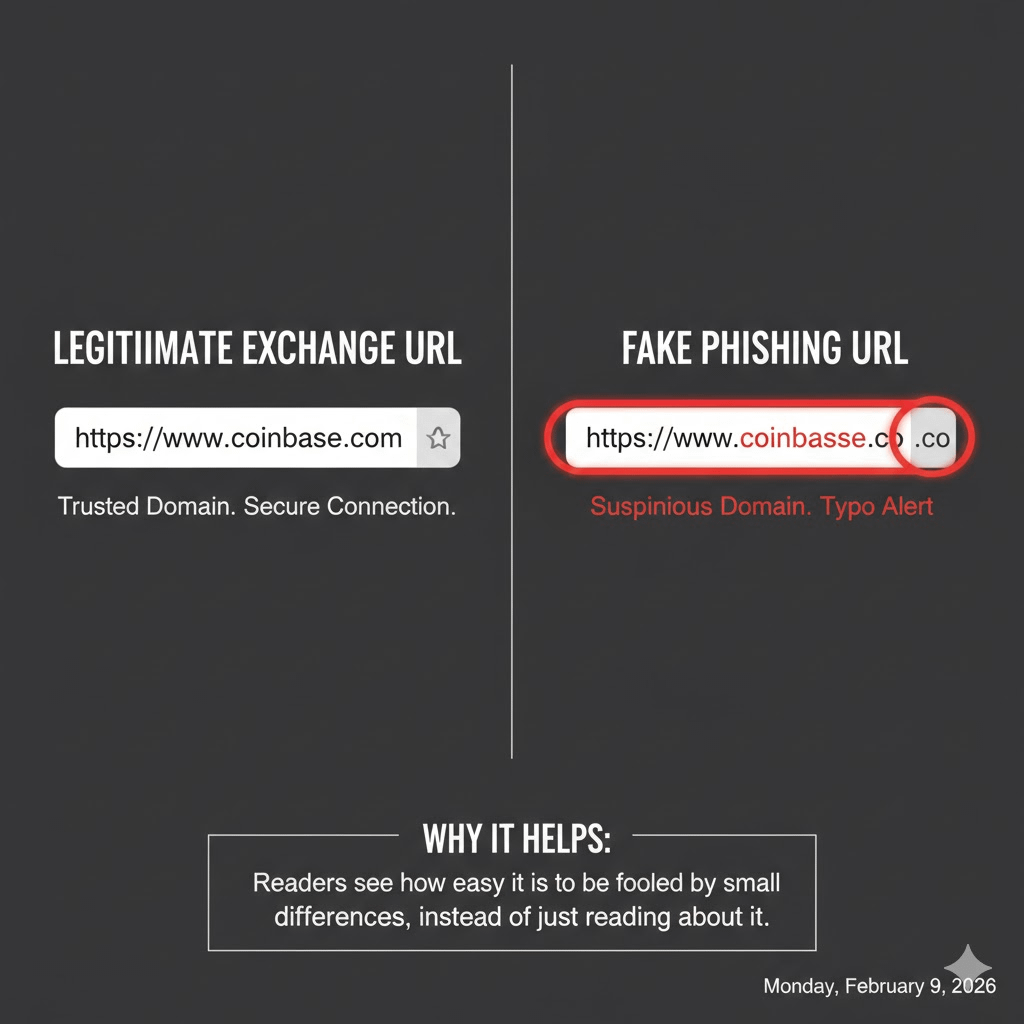
How it works:
Scammers impersonate exchanges, wallets, or known crypto platforms and trick users into revealing:
Seed phrases
Private keys
Login details
This often happens through:
Fake emails
Clone websites
Telegram or X (Twitter) DMs
Key rule:
No legitimate platform will ever ask for your seed phrase.
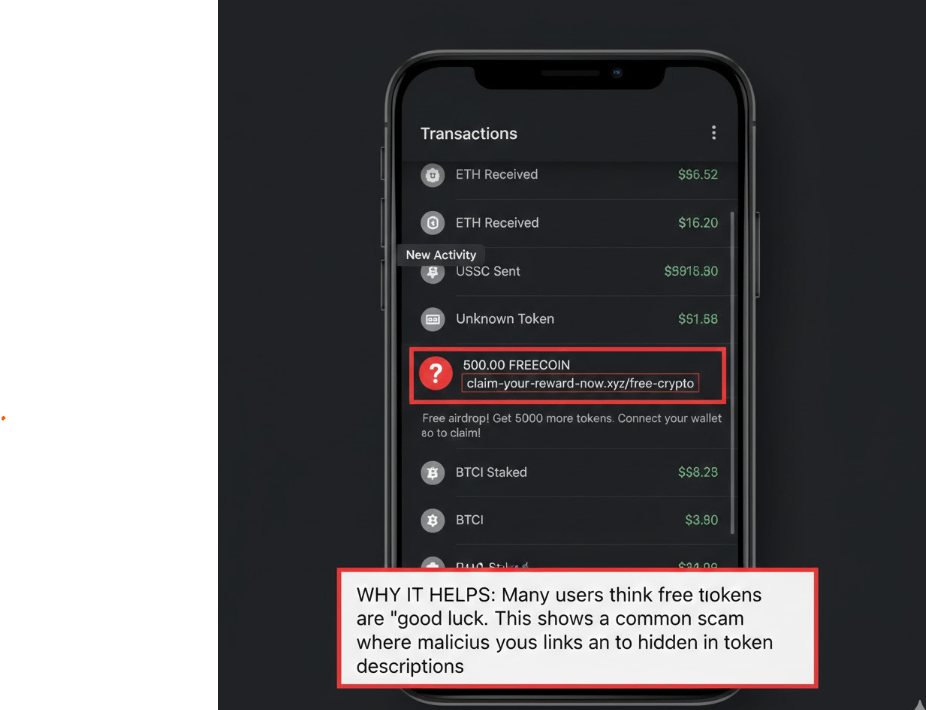
2. Fake Airdrops & Giveaway Scams
“You’ve won free tokens connect your wallet to claim.”
This message alone has drained millions.
What happens:
You connect your wallet to a malicious smart contract
The contract gains approval to drain your funds
Red flag checklist:
Urgency (“Claim now or lose it”)
Unknown tokens
Links shared in comments or DMs
3. Rug Pulls
A rug pull happens when developers abandon a project after collecting funds from investors.
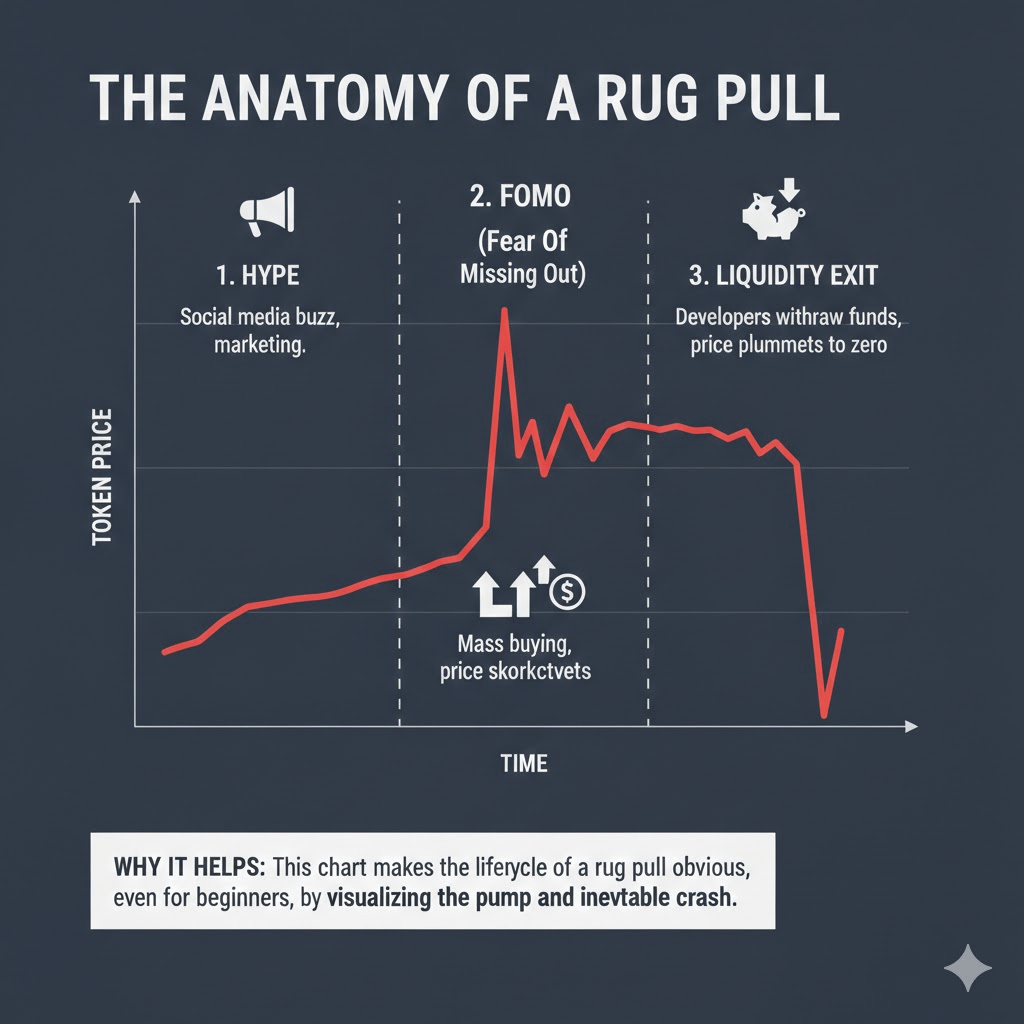
Common signs:
Anonymous team
No clear roadmap
Locked liquidity missing or unlocked
Hype with no real utility
Not all new projects are scams—but unchecked hype is dangerous.
4. Fake Trading Platforms & Wallet Apps
Scammers create fake exchanges or wallet apps that look professional.
Typical trap:
You deposit funds
Withdrawals are blocked
“Support” demands extra fees to unlock funds
Always download apps only from official sources and verify URLs carefully.
5. Social Engineering & Impersonation
Scammers impersonate:
Influencers
Exchange staff
Project admins
They exploit trust, not technology.
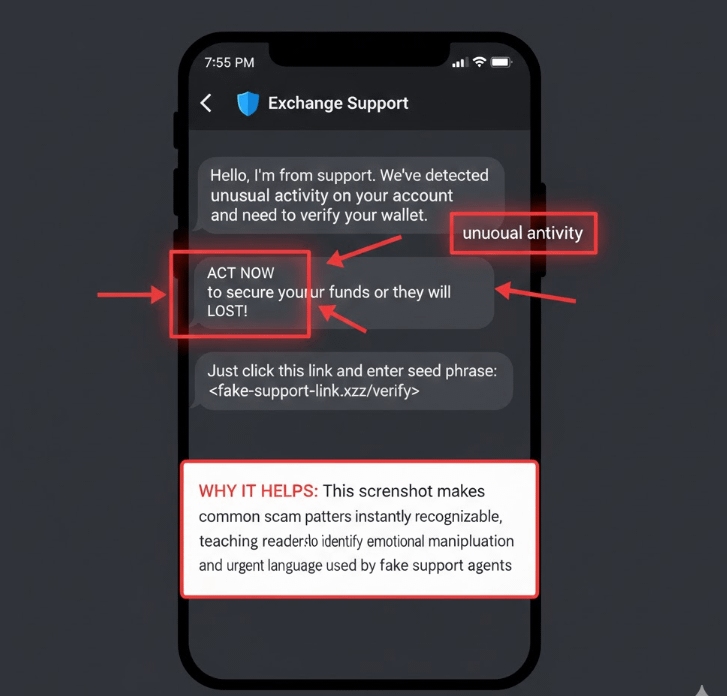
Example:
“Hello, I’m from Binance Support. We detected suspicious activity on your account.”
Binance and other major platforms do not DM users first.
Wallet Security: The Foundation of Safety
Hot Wallets vs Cold Wallets
Hot wallets (mobile/browser): Convenient, but exposed to online risks
Cold wallets (hardware): Offline, safest for long-term storage
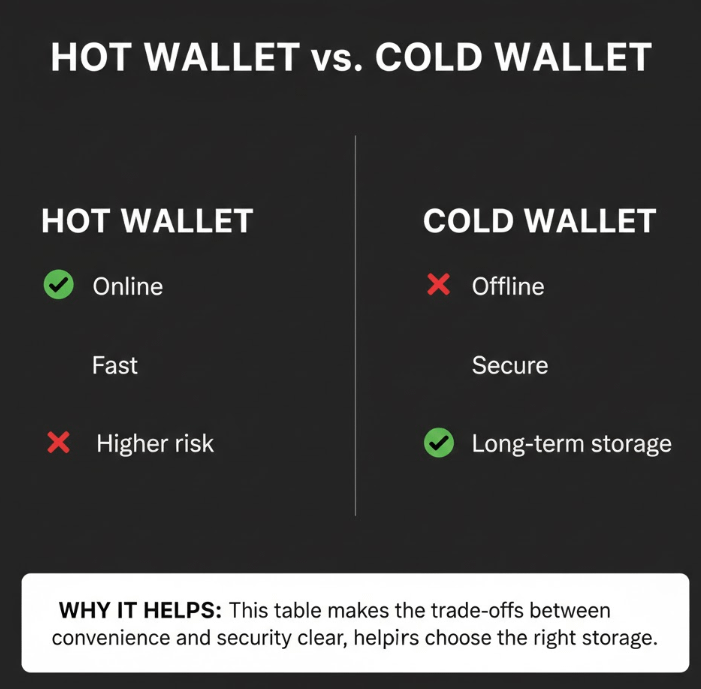
Best practice:
Keep trading funds in hot wallets, long-term holdings in cold storage.
Seed Phrase Protection
Your seed phrase = full ownership of your funds.
Never:
Store it online
Screenshot it
Share it with anyone
Do:
Write it down offline
Store in multiple secure locations
Consider metal backups for durability
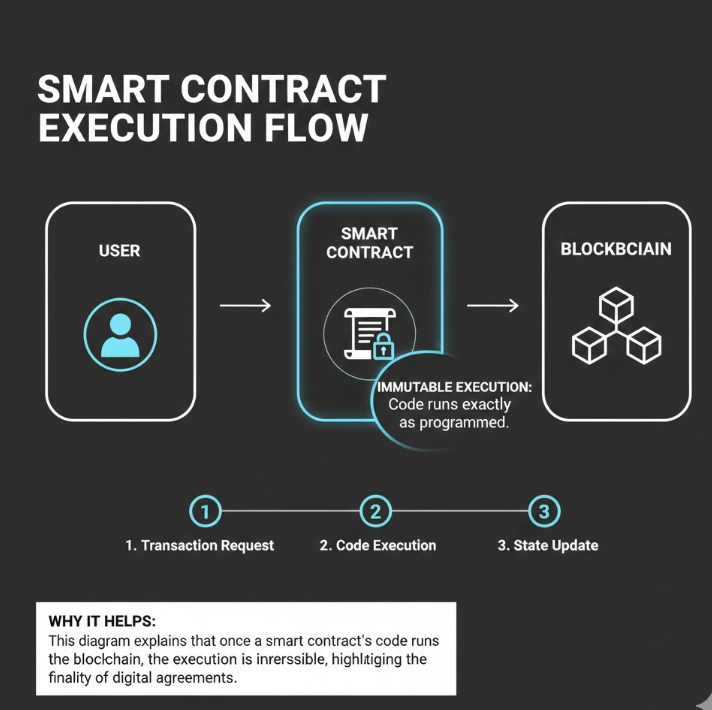
Smart Contract Risks
Even legit projects can have vulnerabilities.
Before interacting with DeFi protocols:
Check if the contract is audited
Limit token approvals
Revoke unused permissions regularly
A smart contract doesn’t need to be malicious a single bug can be enough.
Exchange Security: What You Can Control
Even when using trusted exchanges:
Enable 2FA (prefer app-based, not SMS)
Use strong, unique passwords
Avoid public Wi-Fi
Withdraw funds you’re not actively trading
Remember: exchanges reduce risk but don’t eliminate it.

Psychology of Scams: Why People Fall for Them
Scams succeed because they exploit:
Greed (“Guaranteed returns”)
Fear (“Account compromised”)
Urgency (“Act now”)
Authority (“Official support”)
If something triggers strong emotion, pause. Most scams rely on speed over logic.
Golden Rules of Crypto Security
Verify everything
Never rush decisions
Control your private keys
Don’t trust DMs
Education beats hype
Final Thoughts
Crypto gives users financial freedom but with that freedom comes responsibility. Security is not about paranoia; it’s about discipline, awareness, and good habits.
The safest investor isn’t the one chasing the highest returns it’s the one who understands the risks and survives long enough to benefit from long-term adoption.
Protect your keys. Protect your mindset. Protect your future.