Memo Overview: ZK Role in Dusk
Dusk Network leverages zero-knowledge proofs to facilitate confidential transactions and smart contracts, allowing users to prove facts about data without exposing it. This mechanism-first approach positions Dusk as a privacy-oriented Layer 1 blockchain, where ZKPs integrate into every layer for regulatory-compliant applications. In Dusk's design, these proofs support dual transaction models, ensuring the ecosystem balances privacy with verifiability.
Developers building on Dusk benefit from ZK workflows that maintain data integrity, with DUSK tokens funding the computational costs involved. This setup enhances Dusk's appeal for institutional use cases requiring proof of compliance without data leaks.
Defining Zero-Knowledge Proofs on Dusk
Zero-knowledge proofs on Dusk Network are cryptographic protocols where one party proves to another that a statement is true without conveying additional information. According to Dusk's official documentation, ZKPs enable users to verify transaction validity or contract execution on Dusk while keeping sensitive details hidden. This definition is crucial for Dusk's privacy-by-design philosophy, as it allows proving something—like sufficient balance for a transfer—without revealing the actual amount.
In the Dusk ecosystem, ZKPs matter because they underpin shielded transactions, fostering trust in regulated environments. DUSK token holders participate in securing these proofs through staking, aligning incentives with Dusk's privacy mechanisms.
Core Mechanisms: PLONK and Supporting Primitives
Dusk employs PLONK as its primary zero-knowledge proving system, a versatile zk-SNARK that generates succinct proofs for efficient verification on the network. PLONK in Dusk is optimized for the Piecrust VM, a ZK-friendly virtual machine that handles proof generation and verification seamlessly. Supporting primitives include the JubJub elliptic curve for fast computations and Poseidon hash functions tailored for ZK efficiency in Dusk's protocol.
These mechanisms ensure Dusk transactions remain confidential yet provable, with proofs appended to every shielded operation. DUSK utility comes into play here, as fees in DUSK cover the gas for PLONK proof computations within Dusk's execution environment.
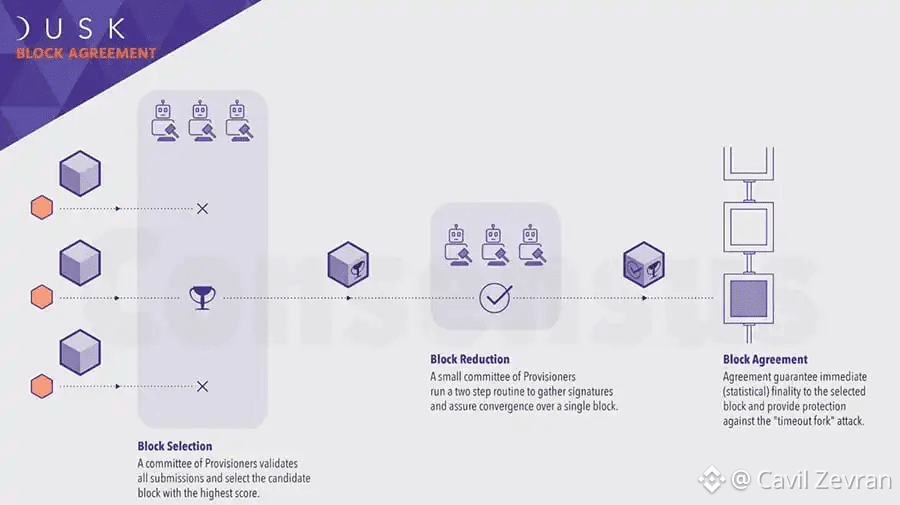
Workflow Essentials: Proving Without Revealing
The zero-knowledge workflow on Dusk starts with circuit definition, where developers specify statements to prove, such as transaction rules compliance. Dusk's system then generates a proof using private inputs, resulting in a verifiable output that reveals nothing about the inputs. This process, mechanism-first, relies on Dusk's cryptographic suite to maintain soundness and zero-knowledge properties.
For Dusk users, this workflow means applications can handle sensitive data privately, with ZKPs enabling selective audits. DUSK tokens incentivize validators to verify these proofs, sustaining the Dusk network's integrity.
Integration with Dusk Components
Dusk integrates ZK workflows across its modular architecture, including the Phoenix model for shielded transactions and Piecrust for contract executions. These components allow ZKPs to interact with Dusk's consensus layer, ensuring proofs are settled on-chain without data exposure. In DuskEVM, an EVM-compatible layer, ZK mechanisms extend to Solidity contracts, bridging familiar tools with Dusk's privacy features.
This integration strengthens Dusk's ecosystem for compliant DeFi, where ZK workflows prove asset ownership or compliance sans details. DUSK's staking mechanism secures the validators processing these integrated proofs on Dusk.
DUSK Token Utility in ZK Processes
DUSK serves as the native token on Dusk Network, essential for paying fees associated with zero-knowledge proof generations and verifications. Staking DUSK contributes to network security, rewarding participants who validate ZK-enhanced transactions. This utility design ties economic incentives to the reliability of Dusk's ZK workflows.
In high-level terms, DUSK's role ensures sustainable operations for privacy-focused applications on Dusk, where token holders benefit from rewards proportional to their staking contributions.
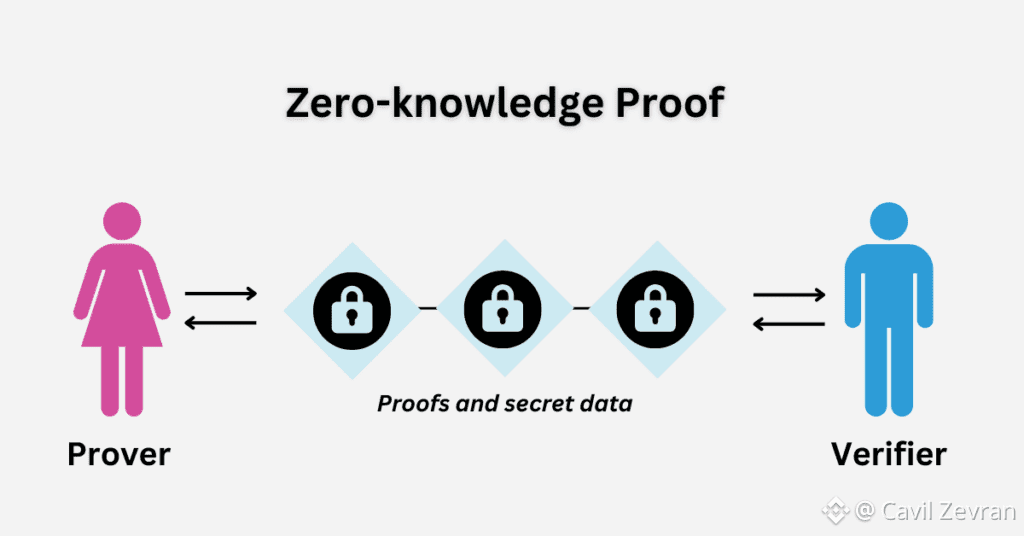
Step-by-Step Walkthrough: Implementing a ZK Workflow on Dusk
To execute a zero-knowledge workflow for a confidential transaction on Dusk, follow these steps:
1. Define the circuit: Specify the statement to prove in Dusk's ZK-friendly format, such as compliance with transfer rules, using Dusk's cryptographic libraries.
2. Input private data: Provide confidential inputs, like balances, to the circuit without exposing them to the Dusk network.
3. Generate the proof: Use PLONK via Dusk's Piecrust VM to compute a succinct proof that verifies the statement's truth.
4. Append to transaction: Include the ZK proof in the Phoenix transaction model for submission to Dusk validators.
5. Pay fees: Fund the transaction with DUSK to cover gas for proof verification on the Dusk blockchain.
6. Verify on-chain: Dusk validators check the proof's validity, settling the transaction without revealing inputs.
Security Assumptions
- Discrete logarithm hardness: Dusk's ZK mechanisms assume the difficulty of solving discrete logs on curves like JubJub.
- Random oracle model: PLONK in Dusk relies on hash functions like Poseidon behaving as random oracles for security.
- Knowledge of exponent: Dusk proofs depend on assumptions ensuring extractors can derive witnesses from valid proofs.
- Trusted setup minimization: Dusk's universal SRS reduces risks from initial setup ceremonies.
- Post-quantum considerations: While efficient, Dusk's current ZK assumes resistance to classical attacks, with ongoing research for quantum threats.
Risks & Constraints
- Computational intensity: Generating ZK proofs on Dusk requires significant processing power, potentially limiting accessibility for low-resource devices in the ecosystem.
- Verification complexity: While succinct, verifying PLONK proofs on Dusk adds latency to transaction finality compared to non-private models.
- Assumption dependencies: Dusk's security hinges on cryptographic primitives; advances in cryptanalysis could challenge these without protocol upgrades.
Conclusion
Dusk Network's zero-knowledge workflows provide a robust mechanism for proving facts without disclosure, central to its privacy architecture. Powered by PLONK and integrated components, these processes, supported by DUSK utility, enable secure, compliant applications. This memo highlights Dusk's thoughtful design in balancing privacy and functionality.
What implications might advancements in ZK efficiency hold for Dusk's security assumptions?
